 ☰
🔍
☰
🔍
05 décembre 2023
 Posted by Sandeep Patil – Principal Software Engineer, and Irene Ang – Product Manager
Posted by Sandeep Patil – Principal Software Engineer, and Irene Ang – Product Manager

The Android Virtualization Framework (AVF) will be available on upcoming select Android 14 devices. The AVF, first introduced in Android 13 on Pixel devices, provides new capabilities for platform developers working on privileged applications.
With AVF, we are more broadly supporting virtualization to Android. Virtualization is widely used and deployed to isolate workloads and operating systems from each other. It enables efficient scaling of infrastructure, testing environments, legacy software compatibility, creating virtual desktops and much more.
With AVF virtual machines become a core construct of the Android operating system, similar to the way Android utilizes Linux processes. Developers have the flexibility to choose the level of isolation for a virtual machine:
- The workload and data inside the VM is inaccessible (confidential) from the host (Android).
- Even if Android is compromised all the way up to (and including) the host kernel, the isolated VM remains uncompromised.
With an isolated VM, developers now have an alternative to Trustzone for use cases that need isolation from Android without escalated privilege.
Virtual machines and the applications running inside them are far more portable than trusted applets. For example, a Linux-based virtual machine with a Linux-application payload will work on all devices that support AVF. This means that developers can build an application once and deploy it everywhere. VMs also make porting of existing Linux based applications seamless and easy, compared to porting into a Trustzone operating system.
AVF is designed to be lightweight, efficient and flexible. Virtual machines can:
AVF is designed with developers in mind. Virtual machines can be customized to meet specific use-case needs. Developers can deploy any VM payload as long as it conforms to certain boot and communication protocols specified by AVF.
In addition to bringing the power of virtualization to Android and enabling all the possibilities of virtual desktops, sandboxing, AVF’s use of isolated virtual machines can benefit the following common Android use cases (and many more):
AVF provides easy APIs to query the device’s ability to create virtual machines and their supported types, and to set up secure communication channels with these virtual machines from applications and services that create them.
For example, to check for the availability of the AVF APIs, and of isolated and regular VM:
VirtualMachineManager manager =
(VirtualMachineManager)context.
getSystemService(VirtualMachineManager.class);
if (manager == null) {
// AVF not supported
} else {
int capabilities = manager.getCapabilities();
if ((capabilities & CAPABILITY_PROTECTED_VM) != 0) {
// protected VM is supported
}
if ((capabilities & CAPABILITY_NON_PROTECTED_VM) != 0) {
// non protected VM is supported
}
}
Please find additional documentation on AVF and its APIs here.
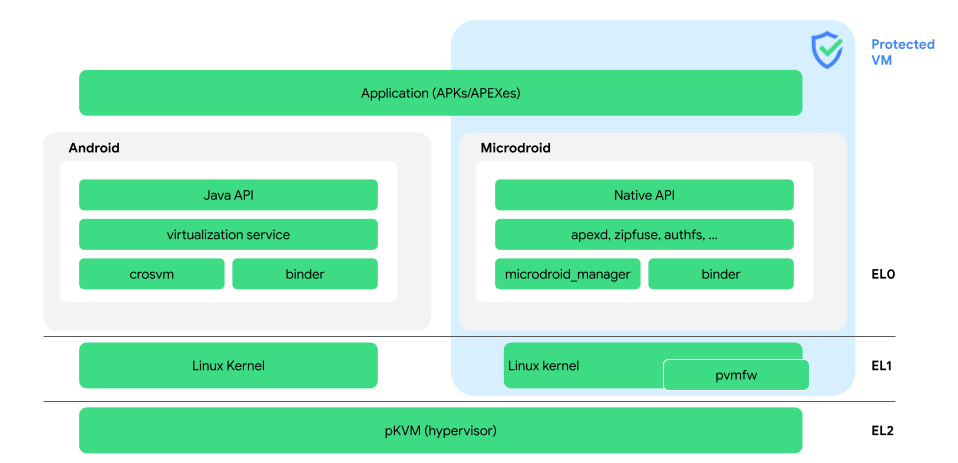
AVF consists of the framework APIs, the hypervisor, and the Virtual Machine Manager. The hypervisor guarantees virtual machines (including Android) are isolated from each other, much like how the Linux kernel does it for processes. The AVF hypervisor (pKVM), however, does that with a significantly smaller (~50x) code base compared to the Linux kernel.
The hypervisor is focused on open source availability, security, device assignment to VMs and security by isolation between virtual machines. It has a small attack surface that meets a higher security assurance level. AVF APIs and features are fully supported by the protected KVM hypervisor (pKVM).
pKVM is built on top of the industry standard Kernel-based Virtual Machine (KVM) in Linux. It means all existing operating systems and workloads that rely on KVM-based virtual machines can work seamlessly on Android devices with pKVM.
crosvm, a Rust-based Virtual Machine Manager (VMM), provides the glue between the hypervisor and the AVF framework. It is responsible for creating, managing and destroying virtual machines. In addition, it provides an abstraction layer across multiple hypervisor implementations.
Isolated virtual machines are invisible to Android i.e. any process running in Android cannot inspect, see, tamper with the content of such a virtual machine. This guarantee is provided by the hypervisor.
Virtual machines are the same as isolated VMs, except they are accessible to Android processes with the right permissions and privilege.
Microdroid is a trimmed down Android OS package that is created to serve as a template for starting a virtual machine (VM). It provides developers with a familiar environment to build and run their workloads in a VM. Microdroid uses familiar Android tools and libraries, such as Bionic, Binder IPC and keystore support.
VirtualizationService manages all guest VMs, isolated or otherwise. It does so, primarily by managing instances of crosvm. It also exposes an AIDL API, which system services or privileged apps can use to start, monitor, and stop VMs.
RpcBinder is an all-new backend developed for the Android Interface Definition Language (AIDL). RpcBinder enables communication to and from virtual machines using the existing binder wire protocol. This means:
Android 14, not only makes AVF available on more devices, it also provides a new toolkit to enable building more with AVF and its components:
Privileged applications can now use VMs for executing their critical workload needing isolation;
Added tracing capability, improved debuggability and monitoring capabilities to provide insights and assist platform developers in developing inside Isolated VMs;
With vendor module extensions, our partners can customize Google’s hypervisor (pKVM) to meet their specific need and differentiate themselves;
With Android 14, a microdroid based VM boots 2 times faster compared to Android 13 while using half the memory.
The rest of the AVF framework makes virtualization easy to use by Android services and apps. For example by abstracting inter-VM communication using AIDL as a transport layer, managing the VM lifecycle or how VMs are created.
The AVF is only for developers of privileged applications and platform developers. TheAndroid Virtualization Framework overview provides a high level guidance on the detailed components of AVF. If you’re an Android Platform developer, try creating a Virtual Machine today and contact us at android-kvm if you have any questions.